AI Regulatory Frameworks: Navigating the New Landscape of AI Governance
As artificial intelligence continues to reshape the cybersecurity landscape, new regulatory frameworks are emerging to ensure responsible development and deployment. For those of us in the field, understanding these regulations is crucial. Let’s break down the key players and what they mean for our day-to-day work.
AI-Powered Threat Hunting: Proactive Security in the Age of Cyber Warfare
Cyber threats are evolving at an unprecedented pace, with attackers leveraging AI to automate their attacks and evade traditional security measures. In response, defenders are turning to AI-powered threat hunting — a proactive approach that detects and neutralizes cyber threats before they can cause damage. In this article, we’ll explore how AI is transforming threat hunting and giving security teams the upper hand.
AI-Powered Deception: The Future of Cybersecurity Misdirection
Cybercriminals are getting smarter, but what if we could outsmart them by making their job harder, or even impossible? Enter AI-powered deception techniques — advanced security strategies designed to mislead attackers, protect assets, and create next-generation honeypots. In this article, we’ll explore how AI is turning deception into a powerful weapon against cyber threats.
AI in Ethical Hacking: Using AI to Outsmart Attackers and Strengthen Cybersecurity
As AI-driven cyber threats grow more advanced, security professionals are turning to AI-powered ethical hacking techniques to counteract malicious activities. This article explores how AI is being leveraged by cybersecurity experts to proactively detect vulnerabilities, enhance penetration testing, and strengthen overall security resilience.
Real-World Case Studies: Countering AI-Powered Social Engineering Attacks
As AI-powered social engineering attacks become increasingly sophisticated, understanding real-world incidents can provide valuable insights into how to defend against them. In this article, we examine notable cases of AI-driven scams, analyze their impact, and highlight the defensive measures that successfully mitigated them.
AI-Powered Social Engineering Defense Strategies: How to Combat AI-Driven Scams and Deception
Introduction As artificial intelligence advances, so do the social engineering attacks that exploit it. Our previous article explored how AI-powered scams manipulate human trust through deepfake audio, video impersonations, AI chatbots, and fake news.
AI-Powered Social Engineering Attacks: What They Mean for Everyday Users and How to Stay Safe
Artificial intelligence has rapidly evolved, bringing groundbreaking benefits — but also new dangers. Among the most concerning developments is AI-powered social engineering, where attackers manipulate human emotions and instincts using sophisticated AI-driven techniques.
Maximizing ROI: The Cost-Benefit Analysis of HITRUST Certification
HITRUST certification is a significant investment for organizations, both in terms of time and financial resources. However, when approached strategically, the benefits of certification — enhanced security, improved compliance, and increased business opportunities — can far outweigh the costs.
The Business Impact of HITRUST Certification: Strengthening Partnerships and Client Trust
Achieving and maintaining HITRUST certification is not just about regulatory compliance — it’s a strategic advantage that can strengthen business relationships and enhance client trust.
Sustaining HITRUST Compliance: Strategies for Long-Term Success
Achieving HITRUST certification is a major accomplishment, but maintaining compliance over time requires ongoing effort and a proactive security strategy.
Navigating the HITRUST Assessment Process: A Step-by-Step Guide
Achieving HITRUST certification is a significant milestone for organizations looking to strengthen their cybersecurity posture and demonstrate compliance with industry regulations.
Implementing HITRUST CSF: A Strategic Approach to Breach Prevention
In today’s evolving cybersecurity landscape, compliance alone isn’t enough — organizations must proactively defend against breaches while maintaining trust with customers, partners, and regulators. That’s where the HITRUST Common Security Framework (CSF) comes in.
Understanding HITRUST Certification: A Comprehensive Guide
In an era where cyber threats and data breaches dominate headlines, organizations need more than just compliance — they need trust. HITRUST certification has become the gold standard for securing sensitive data, particularly in industries like healthcare, finance, and technology.
The Future of U.S. Cybersecurity: Biden’s Executive Order and Trump’s Cyber Plans
As cybersecurity threats evolve, the direction taken by presidential administrations is crucial in shaping national policies that affect everything from federal security measures to how private companies meet compliance regulations.
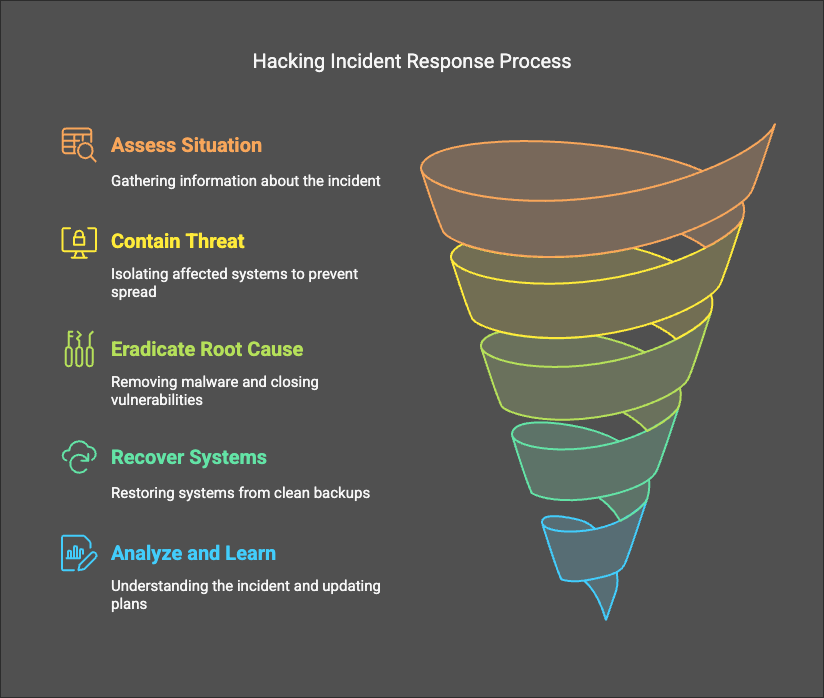
What to Do If You Get Hacked: A Step-by-Step Guide to Regain Control
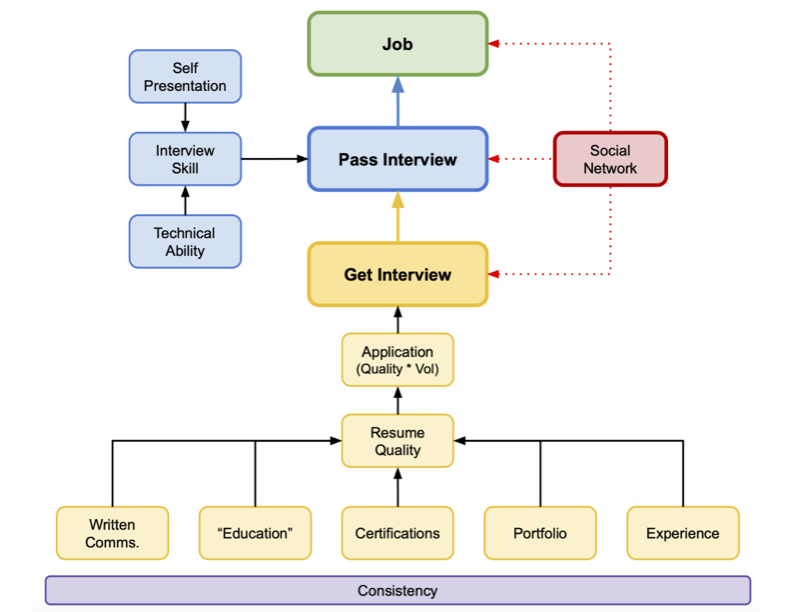
Hacking incidents are becoming more sophisticated, targeting individuals and businesses alike. Your response in the first few hours can mean the difference between full recovery and devastating data loss.Mastering Cybersecurity Employability in 2025: Applying Josh Madakor’s Framework
Josh Madakor’s Employability Framework provides a structured approach to help cybersecurity professionals stand out in this evolving landscape.
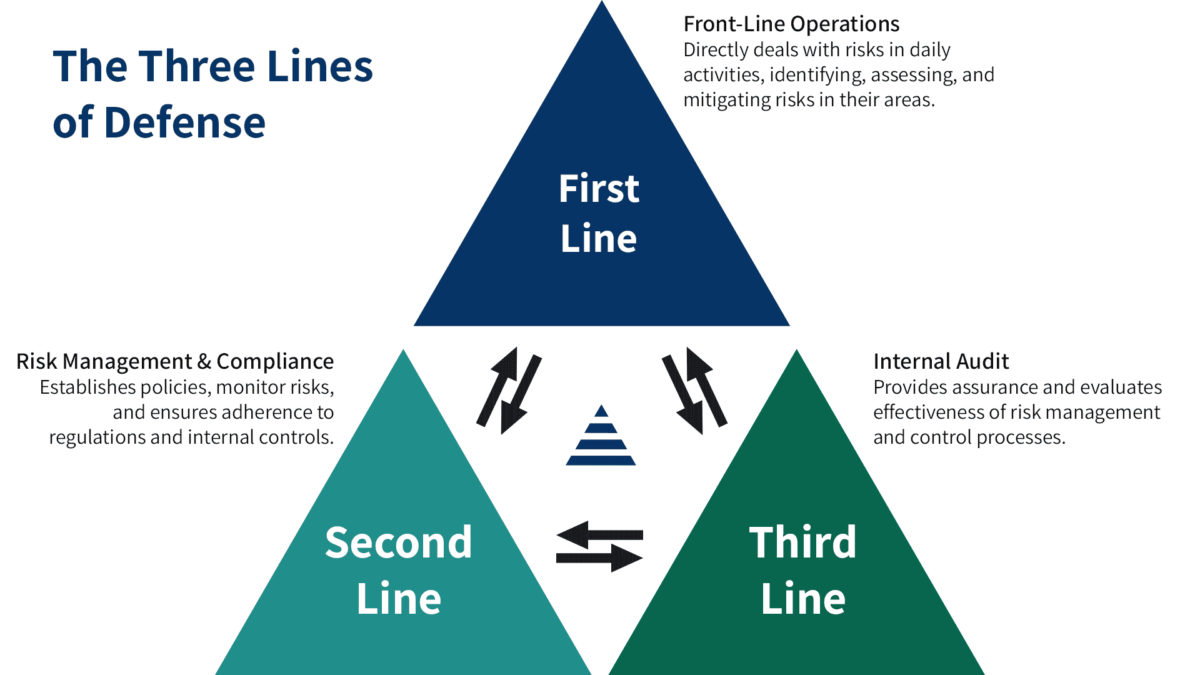
The Three Layers of Audit: Strengthening Organizational Resilience
Audit functions serve as the backbone of risk management and governance in organizations. Whether internal, external, or regulatory, each layer plays a distinct yet interconnected role in ensuring financial integrity, cybersecurity, and operational effectiveness.
Understanding CIS and NIST Frameworks: Cost-Effective Cybersecurity for Every Business
In today’s digital landscape, cybersecurity is no longer optional—it’s a necessity.
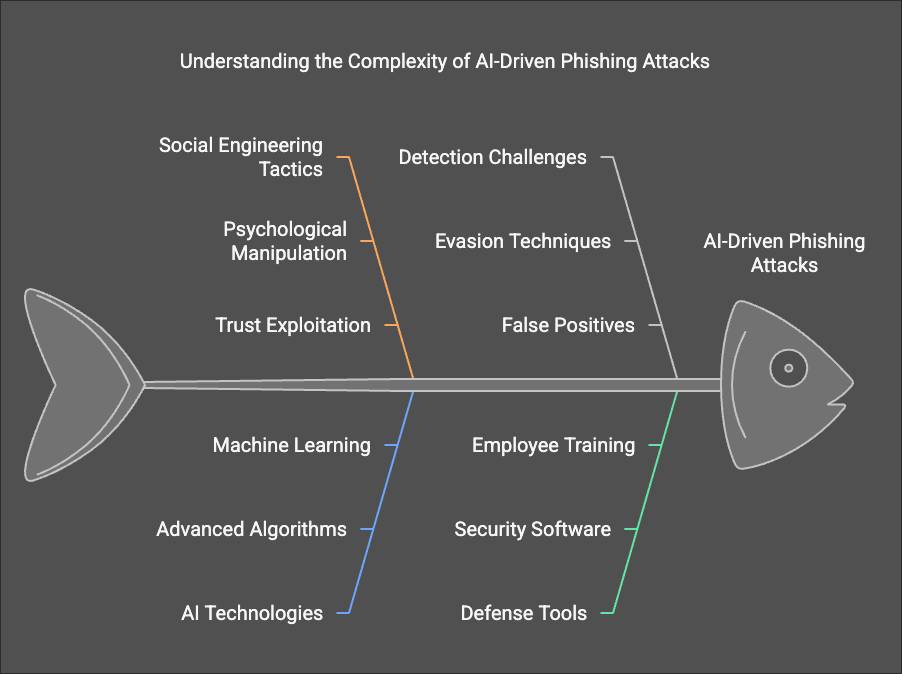
Phishing in the AI Age: Identifying Threats and Equipping Your Company with the Right Tools
Phishing attacks are a cornerstone of modern cybercrime, leveraging social engineering to manipulate individuals into divulging sensitive information or performing actions that compromise security.
DeepSeek Hit by Major Cyberattack Amid Rapid Rise to Prominence
Deep Seek AI hit with cyber attack amid its rise to fame.